
Cyber Security - A Perspective
Manu Sharma, Director - Information Technology And Corporate Security, OnMobile Global Limited | Monday, 14 February 2022, 13:12 IST
 Over past several months, we all, in one way or other, embraced the digital life which is now an integral part of our lives. Covid pandemic outbreak shifted the world order from physical model to virtual mode establishing new normal, which would stay forever. Global trends fast tracked the digitalization by at least 10 years. Unsurprisingly, cyber criminals and hackers became super active as new threats and vulnerabilities are introduced into system. People are no longer operating behind the corporate protections and home networks are extremely weak and open for exploit.
Over past several months, we all, in one way or other, embraced the digital life which is now an integral part of our lives. Covid pandemic outbreak shifted the world order from physical model to virtual mode establishing new normal, which would stay forever. Global trends fast tracked the digitalization by at least 10 years. Unsurprisingly, cyber criminals and hackers became super active as new threats and vulnerabilities are introduced into system. People are no longer operating behind the corporate protections and home networks are extremely weak and open for exploit.
Cyber Threats are Real!
Cyber threat landscape is constantly evolving, there are numerous new created every day and millions created every year. Although the threats follow basic procedures and protocols, they are becoming more potent and frequent.
Online threats are varied and they do not discriminate organizations from individuals when looking for a target.
Cyber attacks can cause massive blackouts, failure of utility services, theft of valuable information, sensitive data like medical records, credit card information, data important for country national security etc. It is not an exaggeration to say that cyber threats may affect the functioning of life, as we know it.
"A cyber-attack surface, which will be an order of magnitude greater than it, is today, and the cyber defenses expected to be pitted against hackers and cybercriminals over that time"
Most common type of Cyber Attacks that gained prominence include targeted Phishing, Ransomware, Denial of service, Social Stigma, Trojans, Malware on Mobile devices.
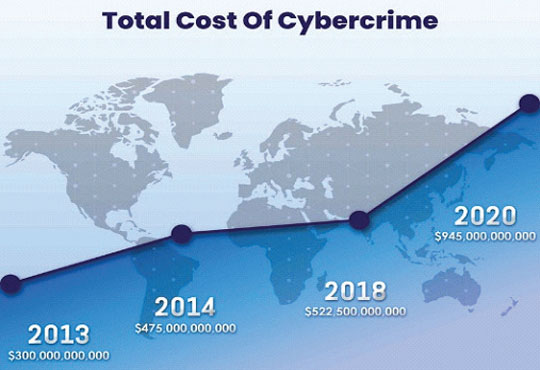
·Cybercrime costs the global economy about1 trillion. It is more than one percent of the global GDP.
·The average cost of a data breach in 2020 was a whopping $3.86 million.
·A data breach compromising 1-10 million records cost $50 million on average, whereas one compromising 50 million records can cost as much as $392 million.
Year 2021 so far has revealed a change in threat landscape and priorities. Attack on Colonial Pipeline in United States is a rude revelation of change in cyber criminal is priorities from individual, corporate based attacks to disrupting the country's mainstream utility services. The role of state based cyberattacks is revealed and hence the situation becomes more hostile.
Many big names of industry have suffered attack of some kind resulting in some kind of loss for them.
CISO and CIO are not only responsible for ensuring implementing security strategies, but are also entrusted to ensure compliance and governance layer is established around the same. Cyber Security is matter of board discussion and a comprehensive integrated strategy to ensure effective safeguards in place is being tested constantly.
How To mitigate the emerging threats and protect the organizations
People as biggest risk Unaware employees can prove to be an organization's biggest weakness when it comes to cyber security. Generating awareness among your employees about the prevalent and emerging cyber threats is one of the most effective ways of protecting your business against cyber attacks.
Phishing incident Response Tool
Educating your employees will only take you so far if we do not equip them with the means of dealing with cyber threats. Empower your employees to detect and report suspicious emails right away, significantly reducing cyber risks
Stick to Basics- Study reveals that 80 percent of threats are effectively mitigated by following basic security protocols like Access management, AV, patch management and regular vulnerability management ensure that possibilities of attacks are reduced largely.
Often, organizations fancy the highend technologies available in market and wrongly estime their need for inception. It is imperative to know the domain, industry vertical and exposure criteria which varies from organization to organization. Understanding the risk appetite, and impact, define the acceptable posture and dynamics of change/ integration for stack to be invested. Else, technologies become overhead or fail to deliver the intended result resulting in massive cost overruns if incepted poorly or in case of misfit.
Third party Risk Management - Make your suppliers, partners, vendors a part of your security strategy and assess the risk and impact emanating from their weak practices. Develop a security framework around the TPRM and make partners accountable for liabilities.
Implement MFA - Enable Multi Factor Authentication (MFA) across all the applicable endpoints of your organization's networks. With majority of employees working from home and using insecure/open networks to connect, security of remote access and application should have an additional layer to prevent damages in case credentials are stolen.
Strong Backup and Restore System - it is not possible to thwart attacks or stop data loss or threats. What is important is ability to recover, both in terms of how fast and latest backup available in system.
Comprehensive Cyber Insurance- is effective in risk transfer and protect organization against monetary loss or legal obligations in case of the breach.
Prepare organization for Remote Working- Trend is here to stay and organization need to look into the way security controls are administered or compliance postures are maintained. A relook into risk probabilities and materialization is mandatory. Identify the changes in policies, processes and technologies to meet the changing requirement and adopt necessary measures.
Year 2021 estimates a total loss of $6 trillion as cost related to cyber threats loss based on historical cybercrime figures including recent year over year growth. This is a dramatic increase. New emerging trends will call for focused approach on security and discipline around the compliances and governance framework. Cost of weak security practices will be very high and organizations should develop an effective governance framework along with an integrated comprehensive security strategy. The magnitude of cyber threats has elevated to state sponsored attacks aimed at toppling the countries economics or cause irrecoverable losses.
A cyber attack surface, which will be an order of magnitude greater than it, is today, and the cyber defenses expected to be pitted against hackers and cybercriminals over that time.
CIO Viewpoint
Marketing Tech - A CIO Perspective
By Satish Panchapakesan, Senior Vice President & CIO, Arvind Fashions
Blockchain Based Cybersecurity For IoT
By Arunmani Subramanian, VP - Emerging Technologies, YASH Technologies
Data Science & Machine Learning In Fintech
By Jainendra Kumar, Head - Global Delivery Center-India & Senior Director Product Development Software, Diebold NixDorf
CXO Insights
Cyber Security - A Perspective
By Manu Sharma, Director - Information Technology And Corporate Security, OnMobile Global Limited
How Low-Code Is Transforming The Future Of Work...
By Deepak Pargaonkar, VP - Solution Engineering, Salesforce
Incorporating Blockchain Capabilities into...



.jpg)









